A Behind the Scenes Look at New Account Fraud
June 24th, 2021

Fraudulent new account applications by cybercriminals and fraudsters have been surging for quite some time. Through identity theft or synthetic identities (combinations of fictitious and real information, such as name, SSN, and other PII to create new identities), threat actors are applying for new accounts at record levels.
This trend has partly been driven by the proliferation of compromised personally identifiable information (PII) and financial account information circulating in the Dark Web, and by Pandemic Unemployment Assistance and Small Business Association (SBA) Paycheck Protection Program (PPP) fraud, which have been extremely popular during the COVID-19 pandemic.
These newly-registered accounts are used in a wide range of financial crimes, including but not limited to:
- Stock manipulation
- Money laundering
- Unemployment fraud
- SBA / PPP loan fraud
- Money mules
- Ad fraud
New Account Fraud: A Russian Cybercriminal Gang Profile
In this post, we take you “behind the scenes” to understand how threat actors create new accounts at scale. We profile a Russian cybercriminal gang that is dedicated to registering accounts across several countries and financial institutions on a massive scale of hundreds of new accounts per day.
For purposes of this post, we named the group the “BlackWidows Group”. The group consists of approximately twenty Russian-speaking cybercriminals, who target financial institutions in the United States and Europe. In the United States alone, BlackWidows Group produces hundreds of new accounts per day.
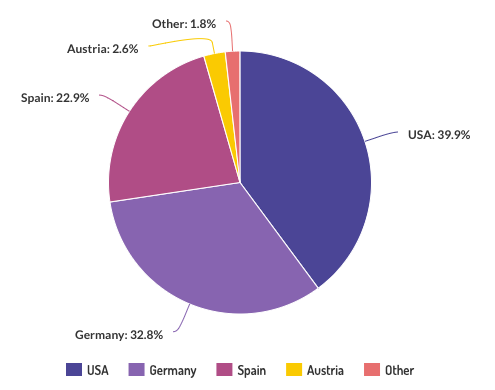
BlackWidows Group newly-registered accounts by country over a two week period in Q2 2021.
The types of accounts opened can be split into three main categories: bank accounts, reloadable prepaid card accounts, and brokerage accounts.
Account Registration Process
The group is extremely efficient and has streamlined its process to perfection. All members adhere to the group’s techniques and procedures, operating as a well-oiled machine and filling daily quotas per country and per bank.
Compiling Identities
The process of registering new accounts begins by obtaining “fullz” – compromised PII (including full name, address, SSN, date of birth, and more) that is readily available for purchase in underground markets. The group compiles identities and related data to be used during account registration.
Next, it is essential to set up an ‘anti-detect’ tool of choice, used to mask the cybercriminal’s identity and bypass anti-fraud measures. The group uses the popular “Indigo Browser”, which has several useful features such as browser fingerprint customization and integration with popular underground proxy providers.
Armed with a stolen identity, a BlackWidows Group member then configures a new “profile” on Indigo Browser and sets the IP address, time zone, language, and geolocation data to match those of the victim. Using an underground proxy provider, the cybercriminal selects a proxy server whose geolocation corresponds to the victim’s physical address.
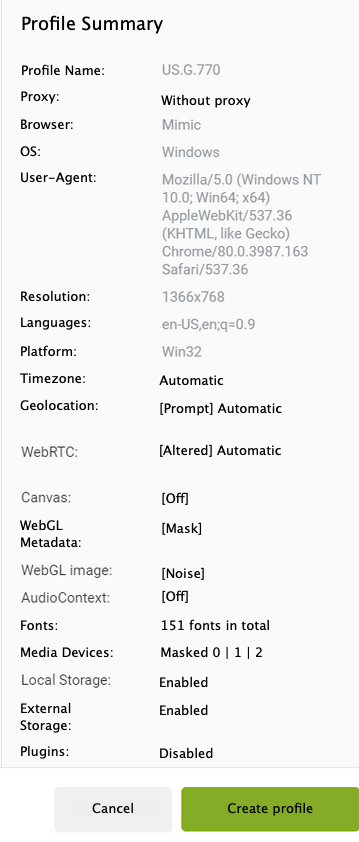
BlackWidows Group’s Indigo Browser “profile” configuration.
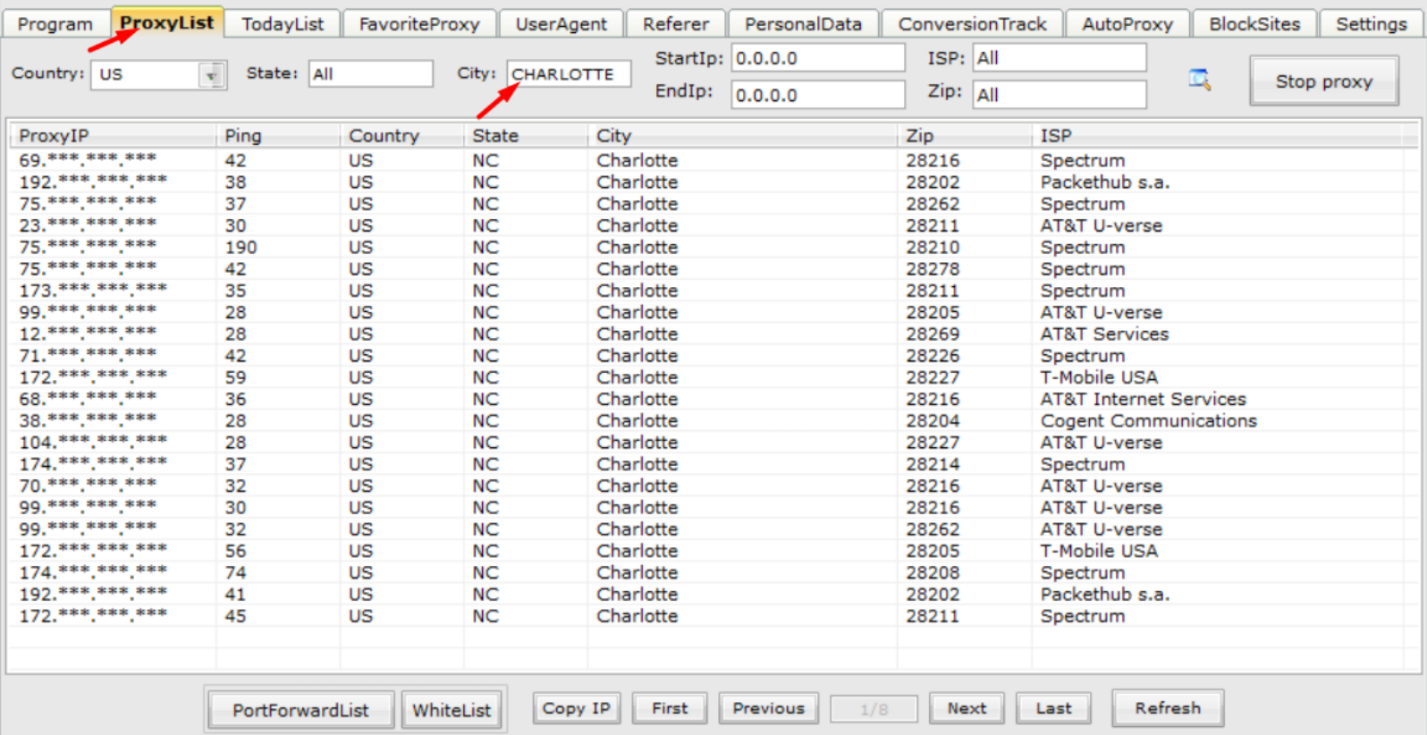
BlackWidows Group using 911 (a popular proxy service in the Russian cybercriminal underground), choosing a proxy server based on the city provided in the victim’s PII.
With technical preparations out of the way, the group proceeds to retrieve the last bit of necessary information – the victim’s phone number. Using legitimate background check services, they search for previous phone numbers used by the victim. Such numbers may be used during the account registration process as they are more likely to pass certain identity verification tools.
The last step is straightforward – creating a new email account to match the victim’s PII and to be used in account applications. BlackWidows Group seems to prefer Outlook and mail.com.
Registering Accounts
At this point, the group can begin self-registering accounts for the stolen identities. The group often uses the same victim PII for registration of accounts at multiple financial institutions. As described above, all the data in the applications accurately belongs to the victim, excluding the contact information – email address and phone number – which is in the group’s control.
It is noteworthy that BlackWidows Group uses a number of services that provide free online SMS receipt for either publicly available numbers or a private number of choice. When two-factor authentication is required for account opening or subsequent activity, the group likely leverages these services to receive the verification messages.
Once the accounts are successfully created, the group sometimes allows them to “age”. The accounts rest with no suspicious activity, and gains a history of seemingly legitimate user login sessions. Aged accounts are more valuable in that they are less likely to trigger anti-fraud controls than newly-registered accounts.
Assessing Your Fraud Risk
Cybercriminals and fraudsters engaged in new account fraud often source PII and synthetic identities via the Dark Web. They also buy and sell such accounts on various Dark Web marketplaces and communities. Finally, they share tools and techniques to carry out new account applications and subsequent fraud at scale. Leveraging intelligence collected from the Dark Web and the broader Digital Underground, organizations could learn of upcoming new account campaigns targeting them, discover recently-opened fraudulent accounts, and spot signals of new account fraud.
Through deep coverage of the Dark Web and the broader Digital Underground, Q6 Cyber monitors:
- Active and recent new accounts registration campaigns.
- Techniques used by cybercriminals for compiling real and stolen identities for account registration.
- The latest technical tools and configurations used to bypass anti-fraud measures.
- Contact emails and phone numbers for authentication.
Additional Resources:
- Find more resources and insights about new account fraud and how to stop stolen and synthetic identity fraud.
- Learn more about how you can monitor the Dark Web when customers are unknowingly compromised.
- Watch a webinar on how we look into the Dark Web, browsing popular fraud and hacker communities.
- Listen to our Let’s Talk FinCrime podcast episode on the Digital Underground, featuring Q6 Cyber founder and CEO Eli Dominitz.




