Combatting Emerging COVID Spoofing Attacks
August 11th, 2020

The COVID-19 pandemic has created unprecedented health and economic concerns worldwide, understandably raising public fear and anxiety, and, in the process, yielding a wide-open playing field to scammers. This blog highlights one of the most prevalent types of scams – COVID spoofing – which comes in many shapes and sizes.
At its core, spoofing occurs when hackers impersonate known or trusted contacts or sources. Its success relies on the ability of scammers to deceive victims by effectively passing themselves off as someone else. Spoofers disguise their communications, including emails, texts or phone calls, making them appear to come from people or organizations their intended victims trust.
Types of COVID spoofing
- Email Spoofing – Sometimes referred to as phishing, spoofers send emails with a falsified “from” line to trick victims into believing that messages are from employers, friends, banks, or other legitimate sources.*
- Text Message Spoofing – Sometimes referred to as smishing, spoofed text messages may appear to come from trusted sources. They often request that potential victims call a certain phone number or click on a link within the message, with the goal of getting them to divulge personal or other sensitive information.
- URL Spoofing – URL spoofing scammers set up fraudulent websites to obtain information from victims or to install malware on their computers. Victims are directed to sites that look like those of banks, credit card companies, or other reputable sources and are then asked to log in using their user ID and password. If they log in to these phony sites, scammers could use their login information to access their real sites and accounts.
- IP spoofing – These scams hide or disguise the location from which data are being sent or requested online. IP spoofing is used in distributed denial of service (DDoS) attacks to prevent malicious traffic from being filtered out and to hide the attacker’s location. With IP spoofing, hackers can make their traffic appear as though it’s coming from multiple sources, making it much more difficult for potential victims to respond.
- Caller ID Spoofing – Spoofers falsify phone numbers from which they’re calling to get victims to answer their phones. It appears that calls are coming from a legitimate business or government agency, such as the Internal Revenue Service. Note that the IRS won’t call taxpayers to tell them they owe taxes without first sending them a bill in the mail.
COVID spoofing examples
While this blog cannot possibly provide examples of all the types of COVID spoofing attacks, following are several of the most common:
- Perpetrators of COVID email spoofing attacks leverage consumer anticipation of government-driven economic stimulus and tax relief to dupe victims into dropping their guard and clicking on a malicious link. (See following example from the Infosec Institute.)
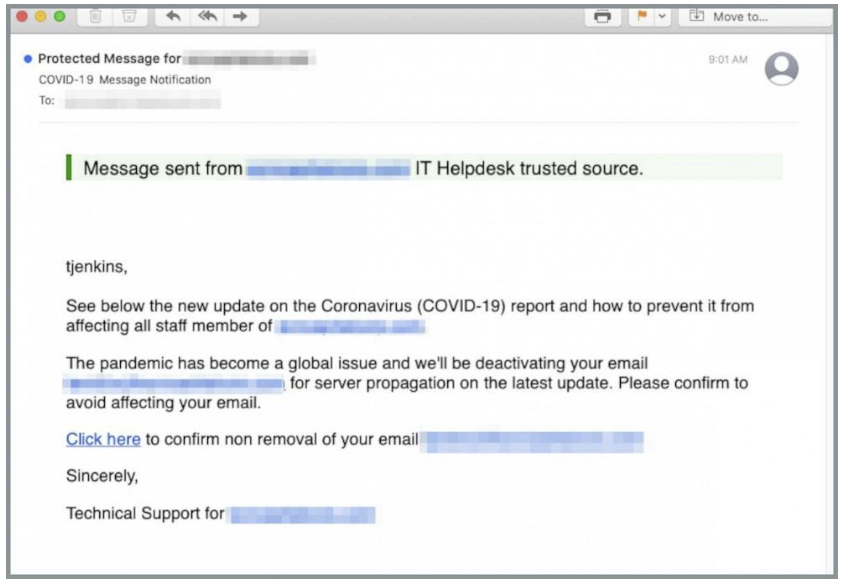
- The pandemic has corporate tech support teams helping employees transition to remote workstations and other nontraditional work settings. Unfortunately, the increased dependence on IT support has given scammers more fertile ground – the impersonation of trusted help desks. (See following example from INKY.)
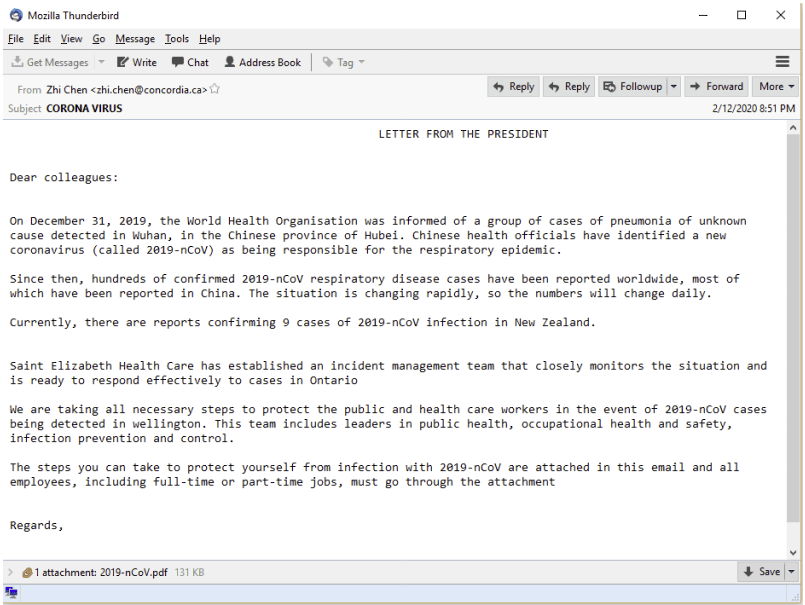
- COVID spoofing also includes impersonating top executives to deliver to employees an attachment disguised as tips to prevent COVID infection. When opened, the attachment infects employee computers and laptops with malware. (See following example from Trustwave.)
- The Better Business Bureau warns of a text message scam impersonating the U.S. Department of Health and Human Services. Recipients are told they must take a “mandatory online COVID-19 test” using a provided link.
- A text highlights “IRS COVID-19 News” and includes instructions and a link to receive payments regardless of their status. The link direct recipients to a spoofed “IRS-like” site and requests identifying personal information, as well as debit or credit card numbers to verify identities.
- One robocall message purports to be from the U.S. Department of Health and Human Services, warning of a COVID outbreak “in your area.” The message recommends getting a vaccine and offers to connect you to a phony “health advisor.”
How to avoid being a COVID spoofing victim
As mentioned, spoofing attacks come in many different forms, but the good news is that their impact can be mitigated or avoided altogether with these general tips and guidelines:
- Be wary of clicking on links. Most COVID spoofing attempts contain an embedded link encouraging you to click it. Hover over any links before clicking through so that you’ll know ahead of time where you’re going. If you are suspicious of the sender, do not open the message and consider deleting it outright.
- Be wary of strange attachments: Never open attachments that you aren’t already expecting to receive, especially if they have abnormal file extensions.
- Call to confirm: If asked to submit personal information, such as a password or credit card number, call the sender to confirm — using the contact number listed on their real website. Manually enter their URL into your browser, check the website for signs of website spoofing, and don’t click any links in the suspicious email you received.
- Change your passwords regularly: If spoofers obtain your login credentials, they won’t be able to do much damage if you already have a new password. Create strong passwords that are hard for others to guess, and use a password manager to store them securely.
- Don’t respond to texts, emails or calls about stimulus checks from the government. The IRS won’t contact you by phone, email, text message, or social media with information about stimulus checks, or ask for Social Security numbers, bank accounts, or government benefits account numbers.
- Verify the sender. Watch for emails claiming to be from the CDC, the WHO or other reputable organizations. Most will NOT ask for any sensitive information through a simple voice, email or text message. If in doubt, contact the organization to confirm that it sent the message and verify its dedicated phone number, email address or text number.
- Keep an eye out for spelling and grammatical mistakes. If email or texts include spelling, punctuation and/or grammar errors, they could be spoofing attempts.
- Ignore offers for vaccinations and home test kits. Spoofers are selling products to treat or prevent COVID without proof that they work. Most test kits being advertised have not been approved by the FDA and aren’t necessarily accurate.
How to report COVID spoofing attempts
If you receive spoofed email or other pernicious communications, let the actual organizations know that they’ve been spoofed. This can help them prevent future spoofing attacks against other unsuspecting consumers. Many organizations have a page on their website where victims can report spoofing and other security issues.
In addition, contact your organization’s IT department and share as much information as possible, including the suspicious email as an attachment, screen grabs from your device or laptop, and the phony email address used by the sender.
Keep in mind that while there are numerous methods to conduct COVID spoofing attacks, they all rely on one common premise: the naiveté of their victims. Consumers and employees who never doubt the legitimacy of websites or never suspect emails or texts of being faked are likely to become spoofing victims.
Encourage employees to approach all emails, texts, websites or phone calls with a critical eye and to contact organizational IT or security teams if there’s any doubt about their authenticity.
For more information about how to protect your organization from COVID spoofing scams and other fraud, learn more about our solutions here.
*Source: Investopedia.com