How Fraudsters Use a Popular Tool to Easily Commit Account Takeover (ATO)
May 5th, 2021

Account takeover (ATO) scams have been growing quickly since early 2020, with estimates ranging from two to six times that of the prior year. While fraudsters carry out these scams in a number of ways, there is one tool of choice for cybercriminals around the world.
The “All-In-One Checker” (AIO) is a simple and user-friendly tool, and has also become popular with underground vendors of compromised account credentials, who use it to build databases of ATO targets and sell these targets to other cybercriminals and fraudsters on various underground marketplaces.
The popularity of AIO and available inventory on markets such as Slilpp suggest that threat actors are pursuing a wide range of fraud and cybercrime ATO-related schemes targeting different industries. Slilpp is one such popular underground marketplace. In total, as of April 2021, Slilpp features approximately 50 million account credentials for sale at the low cost of $2 and $9 per account.
The All-In-One-Checker (AIO) At a Glance
To launch, a user first loads a proxy for anti-detection purposes, and one or more combo-lists containing email credentials (username and password pairs that have somehow been compromised). Additionally, the user specifies keyword strings, i.e., names or URLs of banks, e-commerce shops, cryptocurrency platforms, payment card type, etc. These keywords are the threat actor’s accounts of interest.
With all this information loaded, the user can now run AIO. AIO attempts to authenticate to the email accounts and confirm the existence of the desired online accounts (e.g. banking, e-commerce) based on email communications. AIO then outputs the credentials matching the keyword strings along with the count of matches.
For example, a cybercriminal using AIO inputted a list of keyword strings for certain career sites (@monster.com, @ziprecruiter.com, @simplyhired.com, etc.). Each of the keyword strings in the list was searched within each email account and the results are shown in the screenshot below. Each row includes an email address and password (taken from the combo-list), the match string, and the match count. For example, in the row highlighted in the red box below, the keyword @ziprecrutier matched 684 times in that email inbox.
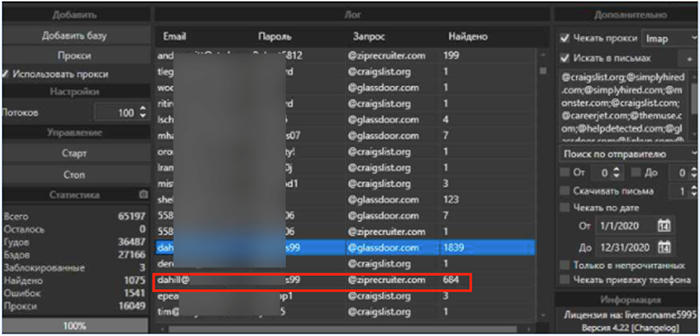
Figure 1 – All-In-One Checker producing results for a search against popular career websites
So what does the cybercriminal or fraudster do with the AIO output? Well, now the threat actor has a list of valid accounts at an online platform or application. In our example above, the threat actor has a list of valid accounts for a career website. The actor visits the career website and requests a password reset for these accounts. The reset request usually triggers an email to the accountholder. Since the actor has access to the email inbox (using the combo-list credentials), the threat actor intercepts the email with the password reset instructions and resets the password. Now the threat actor has complete control of the compromised users’ career website accounts.
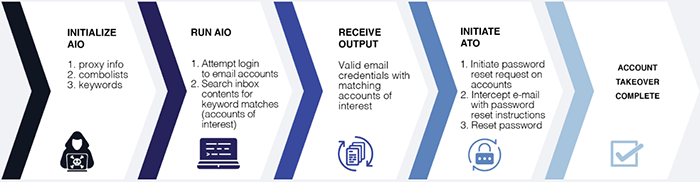
Figure 2 – Step-by-step process for using AIO to execute account takeovers
Other threat actors leverage AIO to build databases of vulnerable accounts (i.e. takeover targets) and then sell them to other cybercriminals, as seen in the screenshot below.
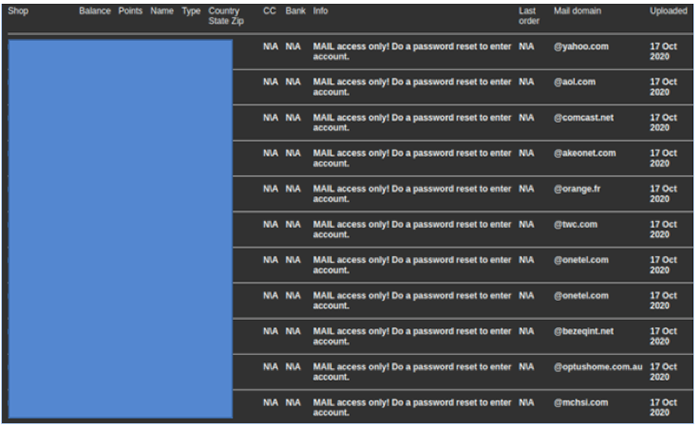
Figure 3 – Thousands of email credentials advertised for sale on a popular account market
As account takeover scams and other frauds continue to grow in our digital world, it’ll be up to the financial crime fighters to stay ahead of the latest tools and practices used by the fraudsters.
Additional resources on monitoring the digital underground:
Learn how you can monitor the Dark Web when customers are unknowingly compromised.




