Orchestrating a Successful Authentication Management Strategy
October 21st, 2020

Balancing security, usability and cost efficiency key to deploying effective authentication management
Organizations are constantly victimized these days by hackers stealing sensitive data, and providing robust network security for clients is more critical than ever. One key to establishing and managing secure systems is implementing security protocols, ensuring that only authorized users have network access. As a result, network authentication methods must be adopted to let legitimate users in while keeping cybercriminals out.
Financial services organizations (FSOs) can implement a wide range of innovative authentication technologies, but in doing so, they must meet their employee and customer demand for simple, frictionless authentication in every channel. To manage and use all the different authentication methods efficiently – i.e., balancing security, usability and cost efficiency – FSOs must adopt a holistic fraud and authentication management strategy. This blog highlights various authentication methods, offering insight on how to determine which ones best meet your needs.
Network Authentication Types
Following is a brief overview of the most common types* of authentication:
- Password authentication – Traditional authentication depends on the use of a password file, in which user IDs are stored together with hashes of the passwords associated with each user. However, experience has shown that even secret passwords are vulnerable to cybercriminal programs that try thousands of potential passwords, gaining access when they guess the right one.
- Two-factor authentication (2FA) – 2FA adds an extra layer of protection to the process of authentication. It requires that a user provide a second authentication factor in addition to the password. 2FA systems often require the user to enter a verification code received via text message on a preregistered mobile phone, or a code generated by an authentication application.
- Multi-factor authentication – Multi-factor authentication requires users to authenticate with more than one authentication factor, including a biometric factor like fingerprint or facial recognition, a one-time code for a phone, a possession factor like a security key fob or a token generated by an authenticator app. These systems are more expensive since they require purchasing new devices, but they can provide an extra measure of security. Most MFA approaches will remember a device. So if users return to use the same phone or computer, the site remembers their device as the second factor. MFA keeps information is safer because hackers would need to steal both passwords and devices.
- Token authentication –Token systems use a purpose-built physical device for the 2FA. This may be a dongle inserted into the computer’s USB port, or a smart card containing a radio frequency identification or near-field communication chip. When deploying token-based systems, FSOs must keep careful track of the dongles or smart cards to ensure they don’t fall into the wrong hands. For example, when workers’ employment ends, they must relinquish their token. These systems also are more expensive since they require purchasing new devices.
- Biometric authentication – While some authentication systems can depend solely on biometric identification, biometrics are usually used as a second or third authentication factor. The more common types of biometric authentication available include fingerprint scans, facial or retina scans and voice recognition. Unfortunately, biometric systems are expensive to install, requiring specialized equipment like fingerprint readers or eye scanners and they come with worrisome privacy concerns, causing users to hesitate to share their personal biometric data.
- Mobile authentication – Mobile authentication is the process of verifying user via their devices or verifying the devices themselves. This lets users log into secure locations and resources from anywhere. The mobile authentication process involves multifactor authentication that can include one-time passwords, biometric authentication or QR code validation.
- One-time password – A one-time password is an automatically generated numeric or alphanumeric string of characters that authenticates a user. This password is only valid for one login session or transaction, and is usually used for new users, or for users who lost their passwords and are given a one-time password to log in and change to a new password.
- Computer recognition authentication –Computer recognition verifies that users are who they claim to be by checking that they are on a particular device. These systems install a small software plug-in on the user’s computer the first time they login. The disadvantage of computer recognition authentication is that users sometimes switch devices. Such a system must enable logins from new devices using other verification methods (e.g., texted codes).
- Single sign-on (SS) – SSO is a useful feature to consider when deciding between device authentication methods. SSO enables a user to only enter their credentials once to gain access to multiple applications. Consider employees who need access to both email and cloud storage on separate websites. If the two sites are linked with SSO, users will automatically have access to the cloud storage site after logging on to the email client, saving users time and improving their experience by avoiding repeatedly entering passwords. Yet it can also introduce security risks, as an unauthorized user who gains access to one system can now penetrate others.
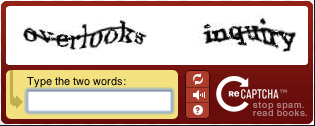
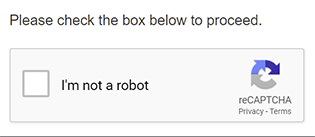
- CAPTCHA authentication –This method does not try to verify specific users, but instead determines whether users are human. The system displays a distorted image of letters and numbers to users, asking them to type in what they see. Computers have a tough time dealing with these distortions, but humans can typically tell what they are. However, they can create some challenges, especially for individuals with disabilities (e.g., sight impaired), who may not be able to get past CAPTCHAs. They can even be frustrating for non-disabled users, leading to delays and possibly causing them to give up trying to access their network. Following are two typical examples of CAPTCHA authentication:
Authentication Management Strategy
With the abundance of authentication methods like those listed above, FSOs often find themselves running disparate tools without a unified cross-channel management or orchestration approach. These siloes can lead to a series of problems, including poor customer experience, ineffective authentication and challenged fraud prevention strategies. The answer is not to avoid authentication innovation, but rather to create an orchestration strategy, which manages policy and execution for multiple authenticators across the contact center, digital channels, ATMs and the branch.
Key to managing authentication projects is establishing objectives, which generally can be divided by areas of access, including workstations; portals or websites; critical business applications (e.g., human resources, accounting, inventory, etc.); and physical locations such as rooms or buildings. In addition, establishing pilot programs (e.g., by location, department, job function, etc.) can be helpful in determining the efficacy of authentication management strategies. Before rolling out across entire organizations, pilot programs can help FSOs realize substantial future savings on both capital investment and operating expenses.
When deploying an authentication management project, it is likely that hardware from several suppliers will have to work together. The objective is to find solutions that make the system as open as possible regarding the technologies used. In fact, having several suppliers can offer advantages. If the overall authentication solution does not depend on one hardware supplier, it can be easier to find workaround solutions with other suppliers when problems arise.
Authentication management strategies will be successful if they’re deployed after carefully considering and planning for all major use cases. By considering day-to-day management at the beginning, strong authentication methods will be accepted by users and unexpected operating expenses can be minimized. In all cases, security needs must be balanced with ease of use as highly secure authentication methods may be rebuffed if they pose too many limitations on employees.
NICE Actimize Authentication-IQ
To help navigate the challenges in developing an authentication management strategy, the Actimize Authentication-IQ solution acts as the brain behind holistic management of multiple authentication methods and risk-based decisions. It creates a complete customer profile, based on historical authentication activity, account servicing, and transactional behavior which is then used to identify suspicious behavior at log-in or throughout a session, producing real-time actionable risk scores.
Authentication management tools manage the process of step up authentication, choosing the appropriate method, producing alerts and enabling real-time interdiction. Further, the solution provides alert and case management in a unified context to prioritize investigations and optimize workflow across the enterprise.
For more information about how your organization can adopt a holistic authentication management strategy, learn more about our solutions here.
* Source: SearchSecurity.com




